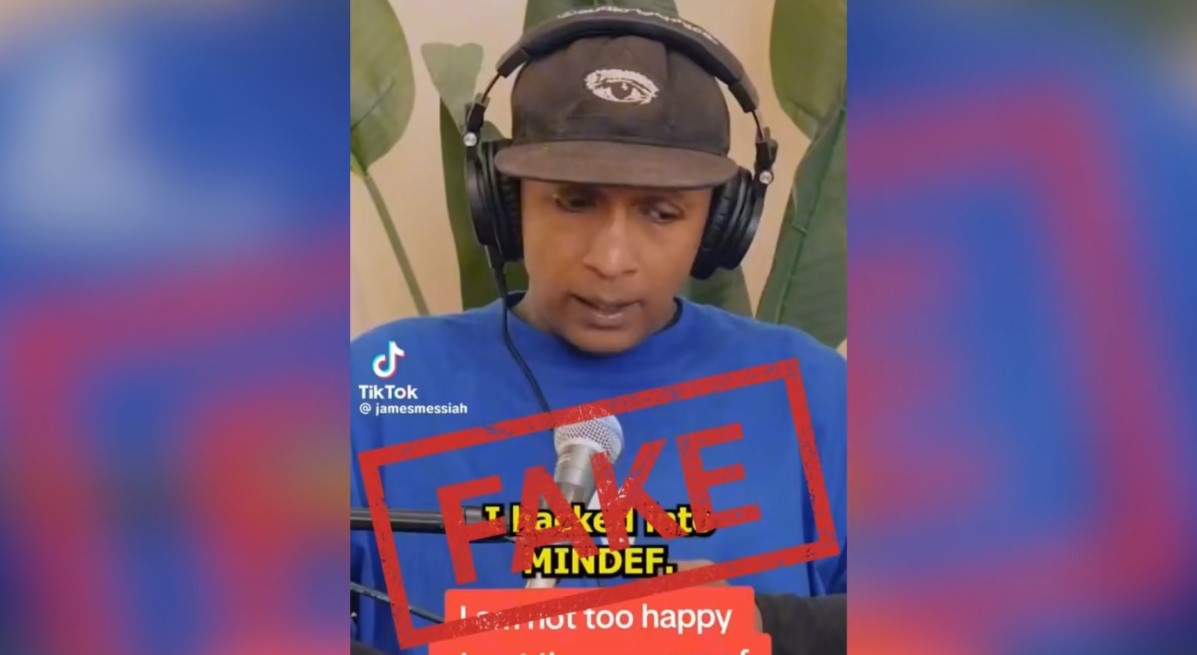
SINGAPORE: The Ministry of Home Affairs has issued correction directions under the Protection from Online Falsehoods and Manipulation Act (POFMA) to a podcast channel for carrying a hacker’s claim that he had breached the Ministry of Defence’s (MINDEF) computer systems.
Hacker James Raj Arokiasamy claimed in an interview with the channel, Plan B, on 6 Sept that he had invaded the computer systems of MINDEF and other Government agencies. He added that his actions had embarrassed the Government.
In a Facebook post on Monday (11 Sept), MINDEF clarified that the hacker’s remarks were untrue and that the Government’s systems were not compromised.
The ministry said: “It has come to our attention that a member of public, James Raj Arokiasamy had claimed to have hacked into MINDEF on a podcast by Plan B which aired on 6 Sep. This is untrue. MINDEF’s systems were neither hacked nor compromised as claimed.”
It added: “MINDEF will continue to stay vigilant and maintain a stringent and proactive approach in detecting and defending against potential cyber threats.”
The MHA has since stepped in, ordering the podcast channel to make corrections on both its Spotify and Instagram accounts.
Noting that three podcast episodes (#614, #615 and #616) which were uploaded to Spotify on Sept 6 contained several false statements made by James, MHA said that some of these false statements were also reproduced on Plan B’s Instagram posts on Sept 7.
MHA said: Plan B will be required to carry correction notices on their Spotify and Instagram accounts. These notices will state that the said podcast and videos contain false statements of fact and provide a link to the Government’s clarification. This will allow readers to read both versions and draw their own conclusions.”
Asserting that the Government takes a serious view of the deliberate communication of malicious falsehoods, MHA added that James had made additional falsehoods and allegations in several TikTok videos. It revealed that TikTok has banned his account and that the videos are no longer accessible.
James, who also goes by the username “James Messiah”, was sentenced to four years and eight months in prison in 2015 for hacking into the websites of at least seven organizations. These include the People’s Action Party Community Foundation, Ang Mo Kio Town Council and City Harvest Church.
The MHA issued a comprehensive statement addressing James Raj’s history and debunking the false claims made in the podcast. It clarified the following key points:
- Charges Against James Raj: James Raj was not arrested due to fear of retaliation, as he had claimed in the podcast. Instead, he was issued a stern warning for an altercation in a shop in 2021. The decision was based on various factors, including the fact that he was not the aggressor and suffered a more serious injury.
- Remand Isolation: James Raj falsely claimed that he was isolated and deprived of human interaction during his remand. The MHA refuted this, stating that he was housed with other inmates during remand and had regular visits from family members and lawyers.
- Reasons for Arrest: Contrary to his claims, James Raj was not arrested for protesting Internet censorship. He was wanted for absconding from bail after being arrested for drug offences and was eventually repatriated to Singapore.
- Plea Deal: The government clarified that James Raj was not offered a plea deal for 39 charges to cover up his hacking activities. He faced a total of 161 charges, of which 40 were proceeded with. The systems he hacked into were publicly disclosed in the charges.
- Hacking into SLA’s Systems: There was no evidence of James Raj hacking into the Singapore Land Authority’s systems. Investigations revealed that he had scanned SLA’s servers but did not successfully breach them.
- Hacking into MINDEF’s Systems: MINDEF’s cyber and security agencies confirmed that James Raj never breached their systems.
MHA added, “We advise members of the public not to speculate and/or spread unverified rumours. The Government takes a serious view of the deliberate communication of malicious falsehoods.”
Read also:
China denies US allegations over military ‘hackers’ – Singapore News